azure-and-aad-articles
Azure Cloud learning resources
Labs
- 2022-03-11 Microsoft Certifications Microsoft Docs
Earn certifications that show you are keeping pace with today’s technical roles and requirements. Select a job role to discover certification paths. Github: Microsoft Learning
- 2022-03-11 AZ500-AzureSecurityTechnologies
labs files. Github: MicrosoftLearning/AZ500-AzureSecurityTechnologies: Microsoft Azure Security Technologies
========== Azure Active Directory ==============
Good Reads Azure Active Directory
- 2022-02-03 Azure AD Outage Analysis: December 15, 2021
ThousandEyes detected a widespread Azure Active Directory (AD) outage lasting ~1.5 hours from ~00:50 UTC – 2:25 UTC, which may have impacted users around the globe from signing in to Microsoft services like O365. During the outage, authentication requests were returning HTTP 503 service unavailable errors.
- 2022-03-05 New Azure Active Directory password brute-forcing flaw has no fix Ars Technica
- 2022-03-16 Architecture overview - Azure Active Directory Microsoft Docs
Azure Active Directory (Azure AD) enables you to securely manage access to Azure services and resources for your users. Included with Azure AD is a full suite of identity management capabilities. For information about Azure AD features, see What is Azure Active Directory? Service architecture design Primary replica Secondary replicas Scalability Continuous availability Fault tolerance Data durability Data consistency Service-level backup
Good Reads about Authentication Protocols
- 2022-03-01 Why you probably don't need OAuth2 / OpenID Connect!
You probably do not need OAuth2, nor OpenID Connect. This is a controversial opinion, even more so because my biggest professional achievements are two of the most successful open source projects in the OAuth2 and OpenID Connect world
CSharp Authentication
- 2022-03-06 Advanced techniques around ASP.NET Core Users and their claims – The Reformed Programmer
The AuthP library provides three main extra authorization features to a ASP.NET Core application. They are...
- 2022-02-06 Authentication in ASP .NET Core - DEV Community
This article covers authentication in ASP .NET Core. It tries to explain the concepts and how they relate and also shows some code so you can hopefully add authentication to your own .NET app.
- 2022-04-03 Combining Bearer Token and Cookie Authentication in ASP.NET - Rick Strahl's Web Log
And we're back for another episode in the seedy TV drama that is ASP.NET Authentication. In today's show we'll discuss the mysterious case of combining multiple authentication schemes in a single application. Tune in at 11 for the scary conclusion...
In this post I'll talk about:
- Combining JWT Bearer Token and Cookie Authentication
- Using Manual JWT Tokens
- Using Manual Cookies
- Using only ASP.NET's low level Auth features - not using ASP.NET Core Identity
Tutorials
- 2022-03-10 Build a web app that authenticates users and calls web APIs - Microsoft identity platform Microsoft Docs
Learn how to build a web app that signs users in to the Microsoft identity platform, and then calls web APIs on behalf of the signed-in user.
Azure Active Directory - Random Articles
- 2022-02-25
aadcloudConfigure Azure AD authentication - Azure App Service Microsoft DocsThis article shows you how to configure authentication for Azure App Service or Azure Functions so that your app signs in users with the Microsoft identity platform (Azure AD) as the authentication provider.
- 2022-01-11 🌤️ Continuous access evaluation in Azure AD Microsoft Docs
- 2022-01-11 🌤️ aad-app-credential-tools/azuread-application-credential-assessment-powershell-guide.md at main · microsoft/aad-app-credential-tools
Microsoft Graph Reference Documentation
- 2022-03-04 Class ContractsConstants.IdentityProperties
Some generated with DocFX MS Graph SDK doc; not bad, but not perfect. Document your source code with comments and get a website for free!
- 2022-02-23 Microsoft Graph permissions reference - Microsoft Graph Microsoft Docs
All Microsoft Graph Permissions
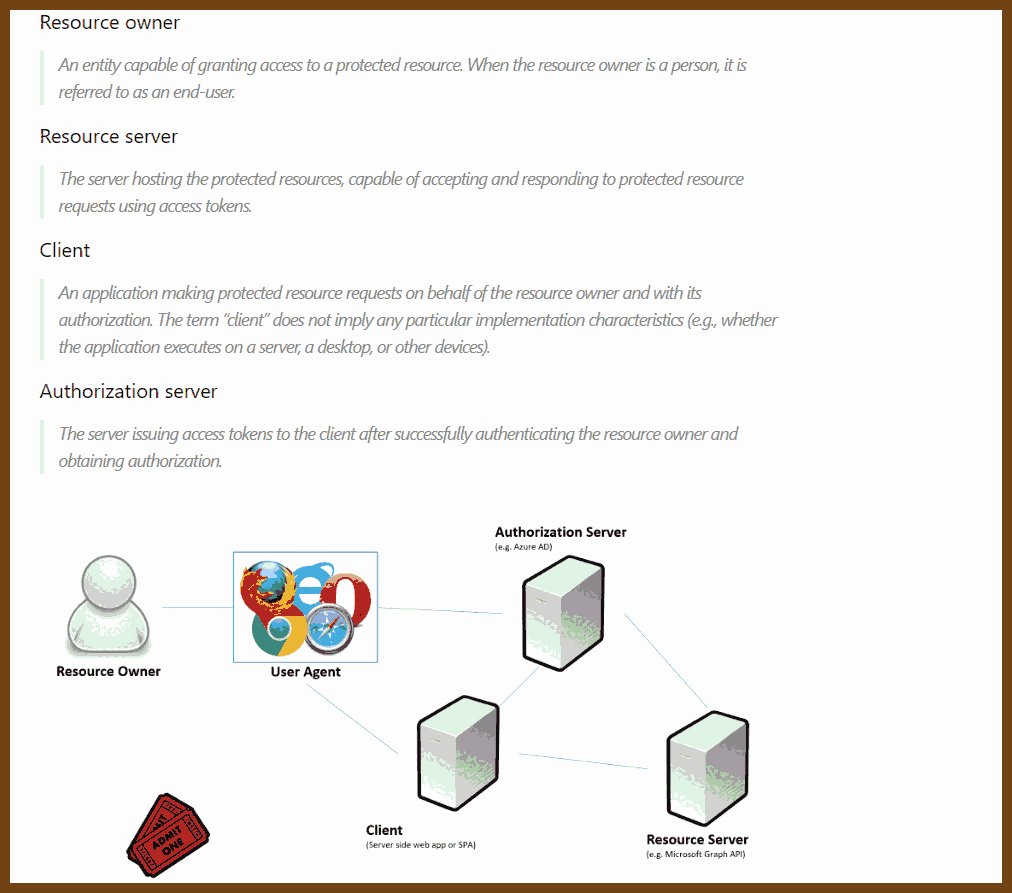
Azure Active Directory Authentication Protocols
OAuth2.0, OpenID Connect, SAML, JWT
JWT
JSON Web Token
- 2022-03-01 Anatomy of a JWT - FusionAuth
Here’s a JSON Web Token, freshly minted. Newlines have been added for clarity, but they are typically not present. And overview of JSON Web Token structure
2023-02-05 Handling JWTs: Understanding Common Pitfalls - Bruce MacDonald, InfraHQ - YouTube
Ensure that the JWT is:
- signed with a strong algorithm (e.g. RS256)
- not expired
typclaim is not set toNoneit is difficult to revoke a JWT, not until it expires. some teams use a block-list of revoked JWTs, but this is not a good solution.
2023-05-18 OAuth 2.0 basics - Playground | MSS Architecture
Philippe De Ryck:
- 2023-08-06 AppSec is Too Hard!? - Philippe De Ryck - NDC Security 2022 - YouTube
- 2023-08-06 Forget about OAuth 2.0. Here comes OAuth 2.1 - Philippe De Ryck - NDC Oslo 2022 - YouTube
- 2023-08-06 draft-ietf-oauth-v2-1-08
- 2023-08-06 How Many Days Has It Been Since a JWT alg=none Vulnerability?
- 2023-08-06 Backend For Frontend Authentication Pattern with Auth0 and ASP.NET Core 2023-08-06 Backends for Frontends pattern - Azure Architecture Center | Microsoft Learn 2023-08-06 Sam Newman - Backends For Frontends 2023-08-06 pragmaticwebsecurity.com Recorded sessions 2023-08-06 pragmaticwebsecurity.com Articles
In the context of authentication and authorization, these acronyms refer to specific standards and protocols. Here's an overview:
JAR (JWT-Secured Authorization Request):
- Description: JAR is a method to secure OAuth 2.0 authorization requests using JWT (JSON Web Tokens). This allows the client to send requests in a way that ensures integrity and possibly confidentiality of the authorization request parameters.
- Use: It's used to protect the content of the authorization request, thus increasing the security of the OAuth 2.0 flow.
PAR (Pushed Authorization Request):
- Description: PAR enables the client to request authorization from the authorization server without exposing the parameters to the end-user's user-agent. It essentially allows the parameters to be sent directly to the authorization server, returning a URL that the user-agent can be redirected to.
- Use: This enhances the security of the OAuth 2.0 authorization process by reducing exposure of sensitive parameters to possibly malicious user-agents or intermediaries.
RAR (Rich Authorization Requests):
- Description: RAR is an extension to OAuth 2.0 that provides a way for clients to convey a fine-grained authorization request, using a structured format, both for scope and other authorization parameters.
- Use: This allows for a more detailed and flexible authorization request, suitable for various complex use cases that require more than the basic scopes.
FAPI2 (Financial-grade API Part 2 - Advanced Financial-grade API):
- Description: FAPI2 is a set of security profiles for OAuth 2.0 and OpenID Connect, designed for high-risk scenarios like financial services and payments. It specifies various security requirements and recommendations to ensure that the authorization process is highly secure.
- Use: It's used to provide robust security measures specifically for financial APIs, where high levels of security are needed.
In summary, these terms are all related to enhancing and extending the security and functionality of the OAuth 2.0 protocol, particularly in scenarios that require high levels of security, such as in financial services.
- 2023-08-06 DuendeSoftware/IdentityServer: The most flexible and standards-compliant OpenID Connect and OAuth 2.x framework for ASP.NET Core
The most flexible and standards-compliant OpenID Connect and OAuth 2.x framework for ASP.NET Core 2023-08-06 Securing SPAs and Blazor Applications using the BFF (Backend for Frontend) Pattern - Dominick Baier - YouTube
OAuth 2.0 / OpenID Connect
Good video by Graeme Foster about how AAD OAuth works with demos. Video starts from 16:50
- 2022-03-10 The Modern Guide to OAuth - FusionAuth
I know what you are thinking, is this really another guide to OAuth 2.0? Well, yes and no. This guide is different than most of the others out there because it covers all of the ways that we actually use OAuth. It also covers all of the details you need to be an OAuth expert without reading all the specifications or writing your own OAuth server. This document is based on hundreds of conversations and client implementations as well as our experience building FusionAuth, an OAuth server which has been downloaded over a million times.
- 2022-03-13 An introduction to OpenID Connect in ASP.NET Core
Explains how OpenID Connect works and how it differs from OAuth2.
AAD SAML
- 2022-02-22 AD FS 2.0 RelayState Microsoft Docs
Hi guys, Joji Oshima here again with some great news! AD FS 2.0 Rollup 2 adds the capability to send RelayState when using IDP initiated sign on. I imagine some people are ecstatic to hear this while others are asking “What is this and why should I care?”
AAD SAML Support - General Articles
- 2022-03-10 Tutorial: Azure Active Directory single sign-on SSO integration with Azure AD SAML Toolkit Microsoft Docs
In this tutorial, you'll learn how to integrate Azure AD SAML Toolkit with Azure Active Directory (Azure AD). When you integrate Azure AD SAML Toolkit with Azure AD, you can:
- Control in Azure AD who has access to Azure AD SAML Toolkit.
- Enable your users to be automatically signed-in to Azure AD SAML Toolkit with their Azure AD accounts.
- Manage your accounts in one central location - the Azure portal.
Azure Active Directory Service Principals and Managed Identity
- 2022-02-23 Managed Identity with Azure Automation and Graph API – Stefan Gericke
This will be a small tutorial how to create the Managed Identity for Azure Automation and how to use this identity for example to connect to Graph API. This will helps you to do administrative tasks with sending request to the API endpoints of Microsoft.
- 2022-02-04 Apps & service principals in Azure AD
- 2022-02-04 Single and multi-tenant apps in Azure AD